Configuring MAC-based quick portal authentication
Network requirements
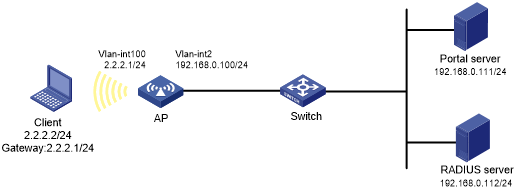
As shown in Figure 98, the client accesses the WLAN through the router. The client is assigned a public IP address either manually or through DHCP. A portal server acts as a portal authentication server, a portal Web server, and a MAC binding server. A RADIUS server acts as the authentication/accounting server.
Configure direct portal authentication, so the client can access only the portal Web server before passing the authentication and can access other network resources after passing the authentication.
Figure 91: Network diagram
Configuration prerequisites
Configure IP addresses for the client, AP, switch, and servers as shown in Figure 98 and make sure they can reach each other.
Configure the RADIUS server correctly to provide authentication and accounting functions.
Configuring the portal server on IMC PLAT 7.1
In this example, the portal server runs on IMC PLAT 7.1(E0303), IMC EIA 7.1(F0303), and IMC EIP 7.1(F0303).
Configure the portal authentication server:
Log in to IMC and click the User tab.
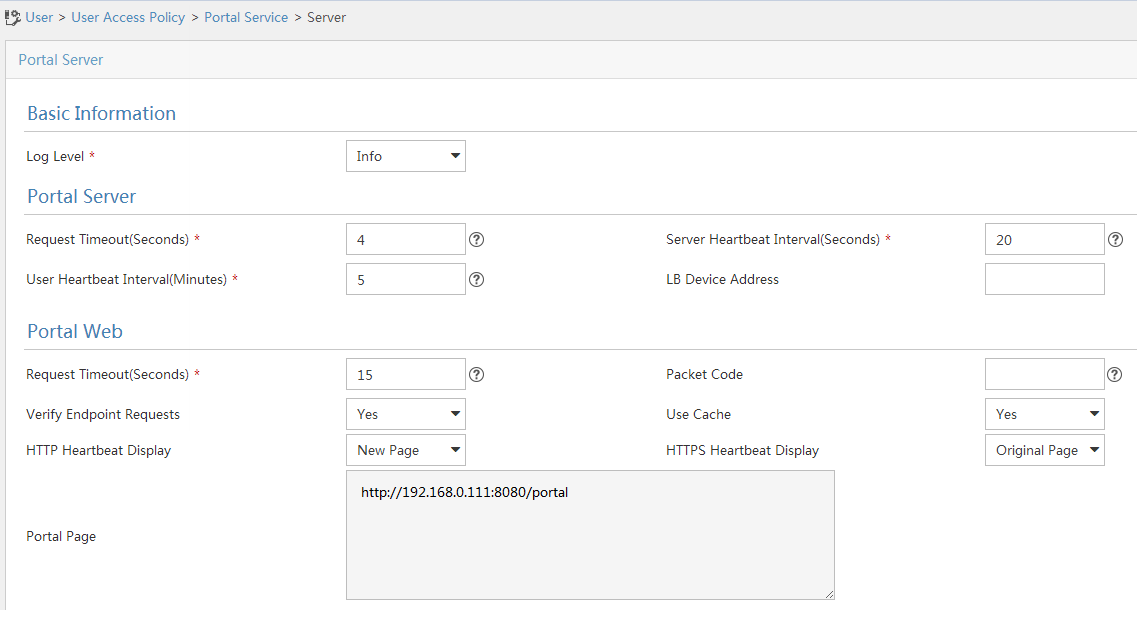
Select User Access Policy > Portal Service > Server from the navigation tree to open the portal server configuration page, as shown in Figure 99.
Configure the portal server parameters as needed.
This example uses the default values.
Click OK.
Figure 92: Portal authentication server configuration
Configure the IP address group:
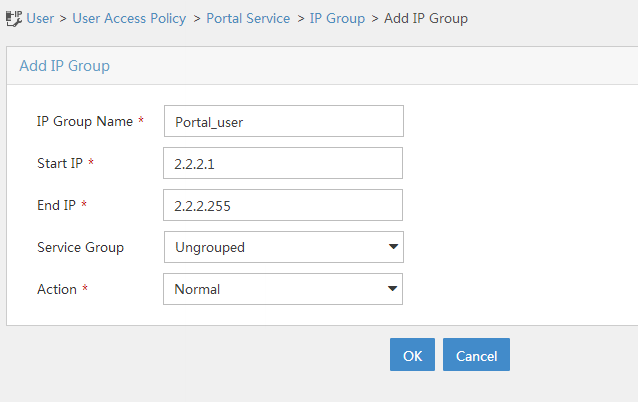
Select User Access Policy > Portal Service > IP Group from the navigation tree to open the portal IP address group configuration page.
Click Add to open the page as shown in Figure 100.
Enter the IP group name.
Enter the start IP address and end IP address of the IP group.
Make sure the client IP address (2.2.2.2) is in the IP group.
Select a service group.
This example uses the default group Ungrouped.
Select Normal from the Action list.
Click OK.
Figure 93: Adding an IP address group
Add a portal device:
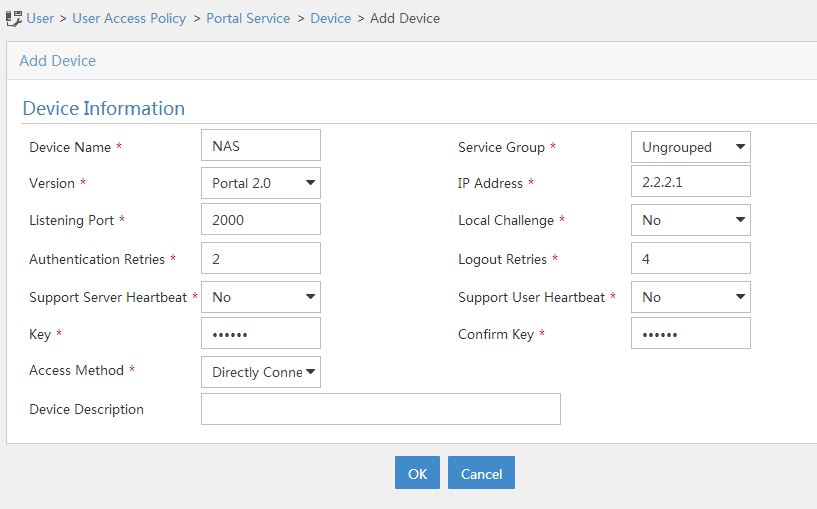
Select User Access Policy > Portal Service > Device from the navigation tree to open the portal device configuration page.
Click Add to open the page as shown in Figure 101.
Enter the device name.
Enter the IP address of the router's interface connected to the client.
Set whether to support the portal server heartbeat and user heartbeat functions.
In this example, select No for both Support Server Heartbeat and Support User Heartbeat.
Enter the key, which must be the same as that configured on the router.
Select Directly Connected for Access Method.
Click OK.
Figure 94: Adding a portal device
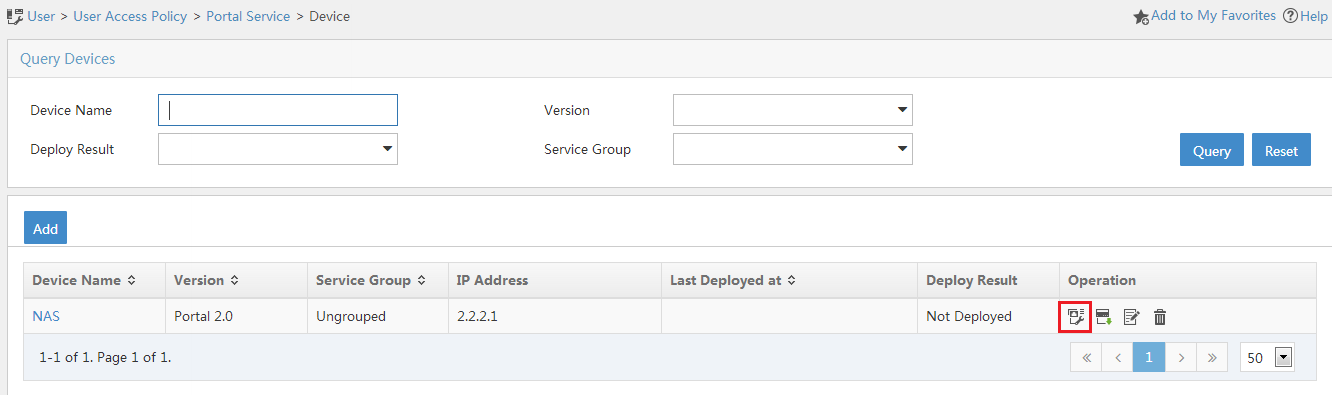
Associate the portal device with the IP address group:
As shown in Figure 102, click the Port Group Information Management icon for device NAS to open the port group configuration page.
Figure 95: Device list
Enter the port group name.
Select the configured IP address group.
The IP address used by the user to access the network must be within this IP address group.
Select Supported for Transparent Authentication.
Use the default settings for other parameters.
Click OK.
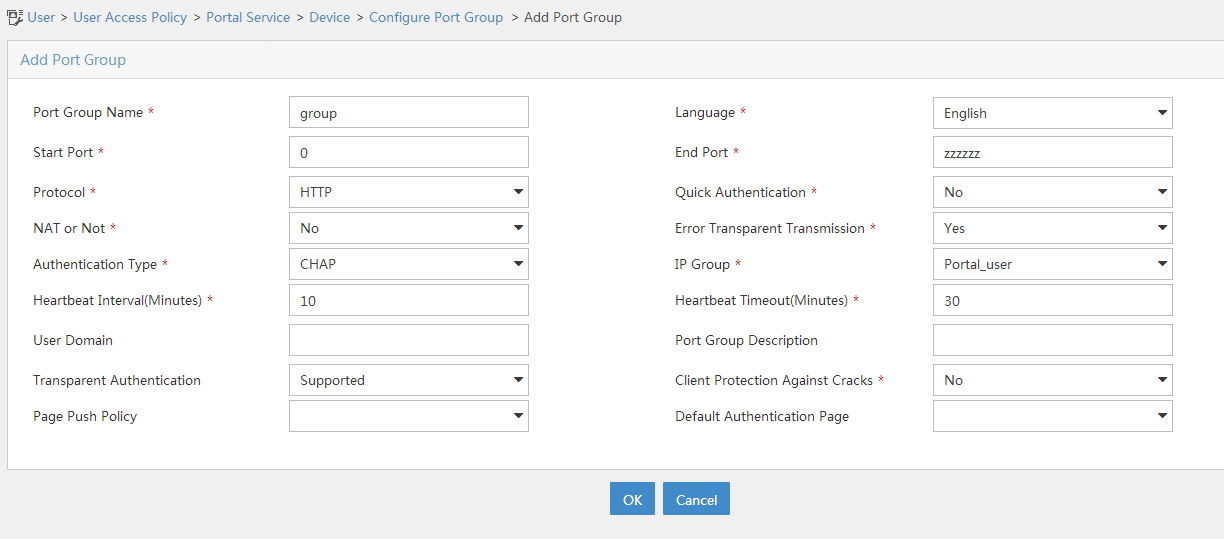
Click Add to open the page as shown in Figure 103.
Enter the port group name.
Select the configured IP address group.
The IP address used by the user to access the network must be within this IP address group.
Select Supported for Transparent Authentication.
Use the default settings for other parameters.
Click OK.
Figure 96: Adding a port group
Configuring the MAC binding server on IMC PLAT 7.1
In this example, the MAC binding server runs on IMC PLAT 7.1(E0303), IMC EIA 7.1(F0303), and IMC EIP 7.1(F0303).
Add an access policy:
Select User Access Policy > Access Policy from the navigation tree to open the access policy page.
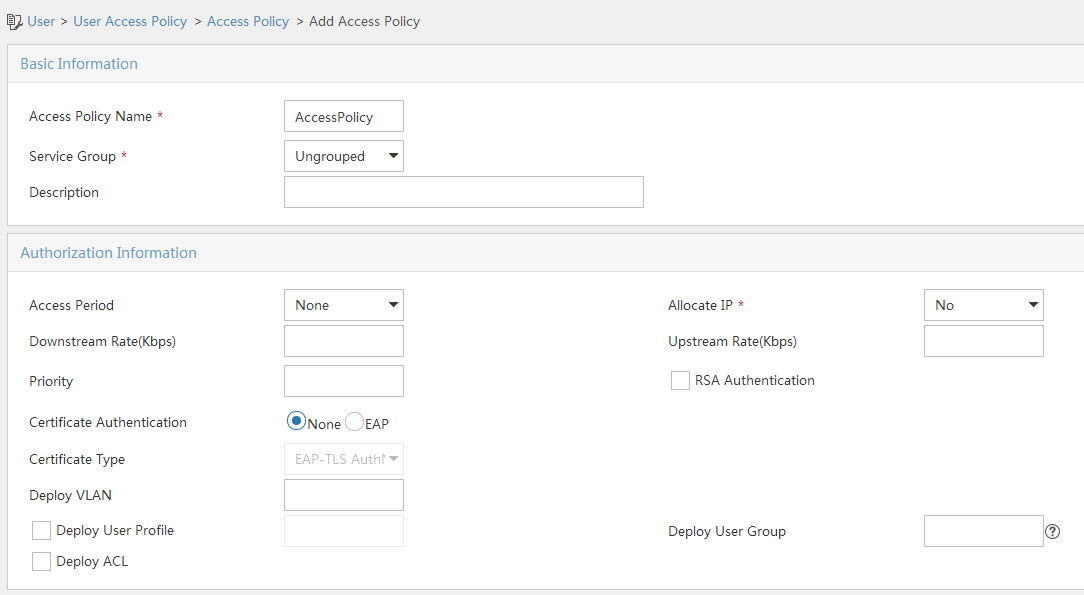
Click Add to open the page as shown in Figure 104.
Enter the access policy name.
Select a service group.
Use the default settings for other parameters.
Click OK.
Figure 97: Adding an access policy
Add an access service:
Select User Access Policy > Access Service from the navigation tree to open the access service page.
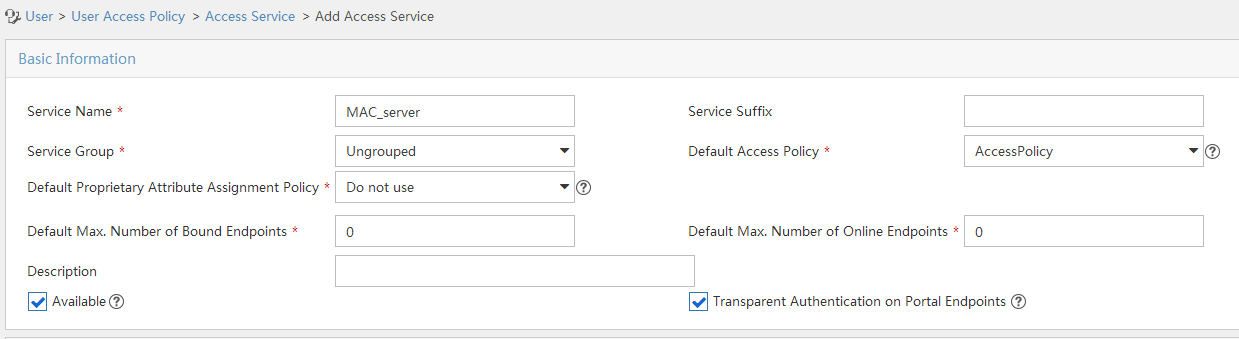
Click Add to open the page as shown in Figure 105.
Enter the service name.
Select the Transparent Authentication on Portal Endpoints option.
Use the default settings for other parameters.
Click OK.
Figure 98: Adding an access service
Add an access user:
Select Access User > All Access Users from the navigation tree to open the access user page.
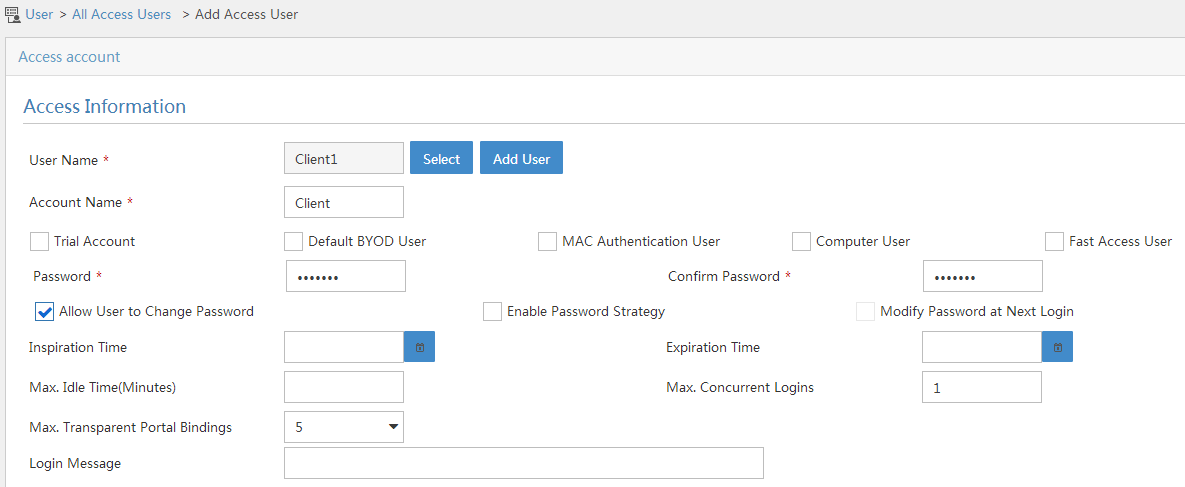
Click Add to open the page as shown in Figure 106.
Select an access user.
Set the password.
Select a value from the Max. Transparent Portal Bindings list.
Click OK.
Figure 99: Adding an access user
Configure system parameters:
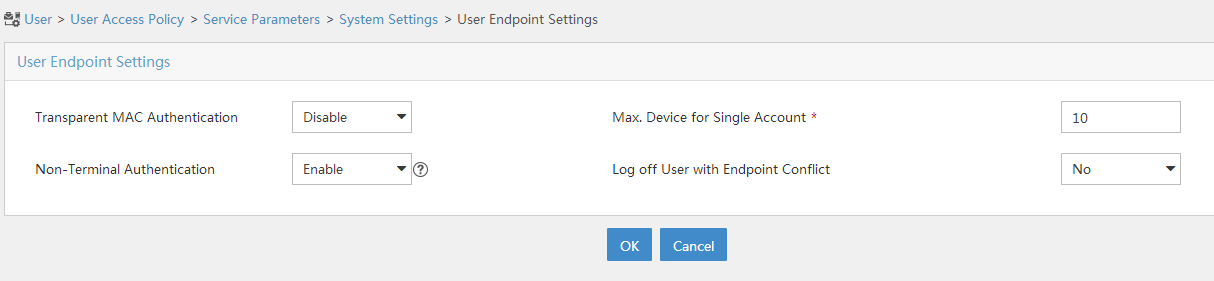
Select User Access Policy > Service Parameters > System Settings from the navigation tree to open the system settings page.
Click the Configure icon
 for User Endpoint Settings to open the page as shown in Figure 107.
for User Endpoint Settings to open the page as shown in Figure 107.Select whether to enable transparent portal authentication on non-smart devices.
In this example, select Enable for Non-Terminal Authentication.
Click OK.
Figure 101: Configuring user endpoint settings
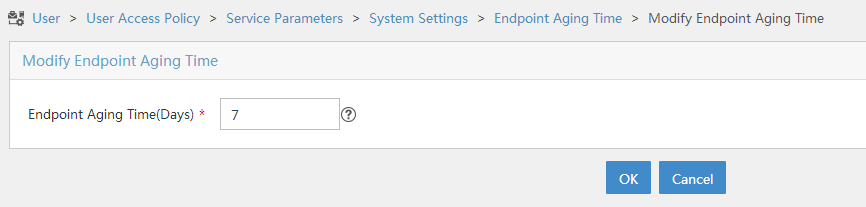
Click the Configure icon
 for Endpoint Aging Time to open the page as shown in Figure 108.
for Endpoint Aging Time to open the page as shown in Figure 108.Set the endpoint aging time as needed.
This example uses the default value.
Figure 103: Setting the endpoint aging time
Configuring the AP
Configure a RADIUS scheme:
# Create a RADIUS scheme named rs1 and enter its view.
<AP> system-view [AP] radius scheme rs1
# Specify the primary authentication server and primary accounting server, and configure the keys for communication with the servers.
[AP-radius-rs1] primary authentication 192.168.0.112 [AP-radius-rs1] primary accounting 192.168.0.112 [AP-radius-rs1] key authentication simple radius [AP-radius-rs1] key accounting simple radius
# Exclude the ISP domain name from the username sent to the RADIUS server.
[AP-radius-rs1] user-name-format without-domain [AP-radius-rs1] quit
# Enable RADIUS session control.
[AP] radius session-control enable
Configure an authentication domain:
# Create an ISP domain named dm1 and enter its view.
[AP] domain dm1
# Configure AAA methods for the ISP domain.
[AP-isp-dm1] authentication portal radius-scheme rs1 [AP-isp-dm1] authorization portal radius-scheme rs1 [AP-isp-dm1] accounting portal radius-scheme rs1 [AP-isp-dm1] quit
# Configure the domain dm1 as the default ISP domain. If a user enters the username without the ISP domain name at login, the authentication and accounting methods of the default domain are used for the user.
[AP] domain default enable dm1
Configure portal authentication:
# Configure a portal authentication server.
[AP] portal server newpt [AP-portal-server-newpt] ip 192.168.0.111 key simple portal [AP-portal-server-newpt] port 50100 [AP-portal-server-newpt] quit
# Configure a portal Web server.
[AP] portal web-server newpt [AP-portal-websvr-newpt] url http://192.168.0.111:8080/portal [AP-portal-websvr-newpt] quit
# Enable validity check on the wireless client.
[AP] portal host-check enable
# Create the service template st1, set the SSID to st1, and create VLAN 100 on the service template.
[AP] wlan service-template st1 [AP-wlan-st-st1] ssid st1 [AP-wlan-st-st1] vlan 100
# Enable direct authentication on the service template st1.
[AP–wlan-st-st1] portal enable method direct
# Specify the portal Web server newpt on the service template st1.
[AP–wlan-st-st1] portal apply web-server newpt
# Configure the BAS-IP as 2.2.2.1 for portal packets sent to the portal authentication server.
[AP-wlan-st-st1] portal bas-ip 2.2.2.1 [AP-wlan-st-st1] quit
Configure MAC-based quick portal authentication:
# Create the MAC binding server mts.
[AP] portal mac-trigger-server mts
# Set the free-traffic threshold for portal users to 1024000 bytes.
[AP-portal-mac-trigger-server-mts] free-traffic threshold 1024000
# Specify the IP address of the MAC binding server as 192.168.0.111.
[AP-portal-mac-trigger-server-mts] ip 192.168.0.111 [AC-portal-mac-trigger-server-mts] quit
# Specify the MAC binding server mts on the service template st1.
[AP] wlan service-template st1 [AP-wlan-st-st1] portal apply mac-trigger-server mts
# Enable the service template st1.
[AP-wlan-st-st1] service-template enable [AP-wlan-st-st1] quit
Verifying the configuration
# Display information about the MAC binding server.
[AP] display portal mac-trigger-server name mts Portal mac-trigger server: mts Version : 1.0 Server type : IMC IP : 192.168.0.111 Port : 50100 VPN instance : Not configured Aging time : 300 seconds Free-traffic threshold : 1024000 bytes NAS-Port-Type : Not configured Binding retry times : 3 Binding retry interval : 1 seconds Authentication timeout : 3 minutes
A user can perform portal authentication by using the HPE iNode client or a Web browser. Before passing the authentication, the user can access only the authentication page http://192.168.0.111:8080/portal. All Web requests from the user will be redirected to the authentication page. After passing the authentication, the user can access other network resources.
For the first portal authentication, the user is required to enter the username and password. When the user goes offline and then accesses the network again, the user does not need to enter the authentication username and password.
# Display portal user information.
[AP] display portal user all
Total portal users: 1
Username: Client1
AP name: ap1
Radio ID: 1
SSID:st1
Portal server: newpt
State: Online
VPN instance: N/A
MAC IP VLAN Interface
0015-e9a6-7cfe 2.2.2.2 100 WLAN-BSS1/0/1
Authorization information:
DHCP IP pool: N/A
User profile: N/A
ACL: N/A
CAR: N/A