Configuring extended direct portal authentication
Network requirements
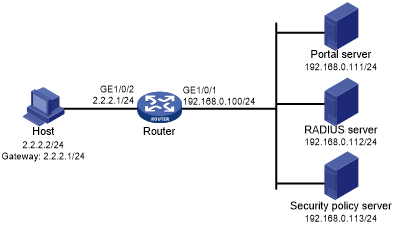
As shown in Figure 69, the host is directly connected to the router (the access device). The host is assigned a public IP address either manually or through DHCP. A portal server acts as both a portal authentication server and a portal Web server. A RADIUS server acts as the authentication/accounting server.
Configure extended direct portal authentication. If the host fails security check after passing identity authentication, it can access only subnet 192.168.0.0/24. After passing security check, the host can access other network resources.
Figure 62: Network diagram
Configuration prerequisites
Configure IP addresses for the host, router, and servers as shown in Figure 69 and make sure they can reach each other.
Configure the RADIUS server correctly to provide authentication and accounting functions.
Configuration procedure
Perform the following tasks on the router.
Configure a RADIUS scheme:
# Create a RADIUS scheme named rs1 and enter its view.
<Router> system-view [Router] radius scheme rs1
# Specify the primary authentication server and primary accounting server, and configure the keys for communication with the servers.
[Router-radius-rs1] primary authentication 192.168.0.112 [Router-radius-rs1] primary accounting 192.168.0.112 [Router-radius-rs1] key accounting simple radius [Router-radius-rs1] key authentication simple radius [Router-radius-rs1] user-name-format without-domain
# Enable RADIUS session control.
[Router] radius session-control enable
# Specify a session-control client with IP address 192.168.0.113 and shared key 12345 in plain text.
[Router] radius session-control client ip 192.168.0.113 key simple 12345
Configure an authentication domain:
# Create an ISP domain named dm1 and enter its view.
[Router] domain dm1
# Configure AAA methods for the ISP domain.
[Router-isp-dm1] authentication portal radius-scheme rs1 [Router-isp-dm1] authorization portal radius-scheme rs1 [Router-isp-dm1] accounting portal radius-scheme rs1 [Router-isp-dm1] quit
# Configure domain dm1 as the default ISP domain. If a user enters the username without the ISP domain name at login, the authentication and accounting methods of the default domain are used for the user.
[Router] domain default enable dm1
Configure ACL 3000 as the isolation ACL and ACL 3001 as the security ACL.
[Router] acl advanced 3000 [Router-acl-ipv4-adv-3000] rule permit ip destination 192.168.0.0 0.0.0.255 [Router-acl-ipv4-adv-3000] rule deny ip [Router-acl-ipv4-adv-3000] quit [Router] acl advanced 3001 [Router-acl-ipv4-adv-3001] rule permit ip [Router-acl-ipv4-adv-3001] quit
![[NOTE: ]](images/note.png)
NOTE:
Make sure you specify ACL 3000 as the isolation ACL and ACL 3001 as the security ACL on the security policy server.
Configure portal authentication:
# Configure a portal authentication server.
[Router] portal server newpt [Router-portal-server-newpt] ip 192.168.0.111 key simple portal [Router-portal-server-newpt] port 50100 [Router-portal-server-newpt] quit
# Configure a portal Web server.
[Router] portal web-server newpt [Router-portal-websvr-newpt] url http://192.168.0.111:8080/portal [Router-portal-websvr-newpt] quit
# Enable direct portal authentication on GigabitEthernet 1/0/2.
[Router] interface gigabitethernet 1/0/2 [Router–GigabitEthernet1/0/2] portal enable method direct
# Reference the portal Web server newpt on GigabitEthernet 1/0/2.
[Router–GigabitEthernet1/0/2] portal apply web-server newpt
# Configure the BAS-IP as 2.2.2.1 for portal packets sent from GigabitEthernet 1/0/2 to the portal authentication server.
[Router–GigabitEthernet1/0/2] portal bas-ip 2.2.2.1 [Router–GigabitEthernet1/0/2] quit
Verifying the configuration
# Verify that the portal configuration has taken effect.
[Router] display portal interface gigabitethernet 1/0/2
Portal information of GigabitEthernet1/0/2
NAS-ID profile: Not configured
VSRP instance : Not configured
VSRP state : N/A
Authorization : Strict checking
ACL : Disabled
User profile : Disabled
IPv4:
Portal status: Enabled
Authentication type: Direct
Portal Web server: newpt(active)
Secondary portal Web server: Not configured
Authentication domain: Not configured
Pre-auth domain: Not configured
User-dhcp-only: Disabled
Pre-auth IP pool: Not configured
Max portal users: Not configured
Bas-ip: 2.2.2.1
User detection: Not configured
Action for server detection:
Server type Server name Action
-- -- --
Layer3 source network:
IP address Mask
Destination authenticate subnet:
IP address Mask
IPv6:
Portal status: Disabled
Authentication type: Disabled
Portal Web server: Not configured
Secondary portal Web server: Not configured
Authentication domain: Not configured
Pre-auth domain: Not configured
User-dhcp-only: Disabled
Pre-auth IP pool: Not configured
Max portal users: Not configured
Bas-ipv6: Not configured
User detection: Not configured
Action for server detection:
Server type Server name Action
-- -- --
Layer3 source network:
IP address Prefix length
Destination authenticate subnet:
IP address Prefix length
Before passing portal authentication, a user that uses the HPE iNode client can access only the authentication page http://192.168.0.111:8080/portal. All Web requests from the user will be redirected to the authentication page.
The user can access the resources permitted by ACL 3000 after passing only identity authentication.
The user can access network resources permitted by ACL 3001 after passing both identity authentication and security check.
# After the user passes identity authentication and security check, use the following command to display information about the portal user.
[Router] display portal user interface gigabitethernet 1/0/2
Total portal users: 1
Username: abc
Portal server: newpt
State: Online
VPN instance: N/A
MAC IP VLAN Interface
0015-e9a6-7cfe 2.2.2.2 -- GigabitEthernet1/0/2
Authorization information:
DHCP IP pool: N/A
User profile: N/A
ACL: 3001
CAR: N/A