ACL assignment configuration example
Network requirements
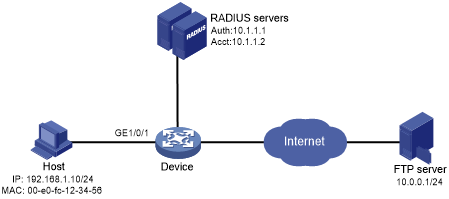
As shown in Figure 50, configure the device to meet the following requirements:
Use RADIUS servers to perform authentication, authorization, and accounting for users.
Perform MAC authentication on GigabitEthernet 1/0/1 to control Internet access.
Use MAC-based user accounts for MAC authentication users. Each MAC address is in the hexadecimal notation with hyphens, and letters are in lower case.
Use an ACL to deny authenticated users to access the FTP server at 10.0.0.1.
Figure 43: Network diagram
Configuration procedure
Make sure the RADIUS servers and the access device can reach each other.
Configure ACL 3000 to deny packets destined for 10.0.0.1.
<Device> system-view [Device] acl advanced 3000 [Device-acl-ipv4-adv-3000] rule 0 deny ip destination 10.0.0.1 0 [Device-acl-ipv4-adv-3000] quit
Configure RADIUS-based MAC authentication on the device:
# Configure a RADIUS scheme.
[Device] radius scheme 2000 [Device-radius-2000] primary authentication 10.1.1.1 1812 [Device-radius-2000] primary accounting 10.1.1.2 1813 [Device-radius-2000] key authentication simple abc [Device-radius-2000] key accounting simple abc [Device-radius-2000] user-name-format without-domain [Device-radius-2000] quit
# Apply the RADIUS scheme to an ISP domain for authentication, authorization, and accounting.
[Device] domain bbb [Device-isp-bbb] authentication default radius-scheme 2000 [Device-isp-bbb] authorization default radius-scheme 2000 [Device-isp-bbb] accounting default radius-scheme 2000 [Device-isp-bbb] quit
# Specify the ISP domain for MAC authentication.
[Device] mac-authentication domain bbb
# Configure the device to use MAC-based user accounts. Each MAC address is in the hexadecimal notation with hyphens, and letters are in lower case.
[Device] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication on GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1 [Device-GigabitEthernet1/0/1] mac-authentication [Device-GigabitEthernet1/0/1] quit
# Enable MAC authentication globally.
[Device] mac-authentication
Configure the RADIUS servers:
# Add a user account with 00-e0-fc-12-34-56 as both the username and password on each RADIUS server. (Details not shown.)
# Specify ACL 3000 as the authorization ACL for the user account. (Details not shown.)
Verifying the configuration
# Verify the MAC authentication configuration.
[Device] display mac-authentication
Global MAC authentication parameters:
MAC authentication : Enable
User name format : MAC address in lowercase(xx-xx-xx-xx-xx-xx)
Username : mac
Password : Not configured
Offline detect period : 300 s
Quiet period : 60 s
Server timeout : 100 s
Authentication domain : bbb
Online MAC-auth wired users : 1
Silent MAC users:
MAC address VLAN ID From port Port index
GigabitEthernet1/0/1 is link-up
MAC authentication : Enabled
Carry User-IP : Disabled
Authentication domain : Not configured
Auth-delay timer : Disabled
Re-auth server-unreachable : Logoff
Host mode : Single VLAN
Max online users : 4294967295
Authentication attempts : successful 1, failed 0
Current online users : 1
MAC address Auth state
00e0-fc12-3456 Authenticated
# Verify that you cannot ping the FTP server from the host.
C:\>ping 10.0.0.1 Pinging 10.0.0.1 with 32 bytes of data: Request timed out. Request timed out. Request timed out. Request timed out. Ping statistics for 10.0.0.1: Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
The output shows that ACL 3000 has been assigned to GigabitEthernet 1/0/1 to deny access to the FTP server.