802.1X with ACL assignment configuration example
Network requirements
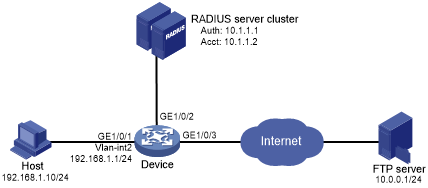
As shown in Figure 44, the host that connects to GigabitEthernet 1/0/1 must pass 802.1X authentication to access the Internet.
Perform 802.1X authentication on GigabitEthernet 1/0/1. Use the RADIUS server at 10.1.1.1 as the authentication and authorization server, and the RADIUS server at 10.1.1.2 as the accounting server.
Configure ACL assignment on GigabitEthernet 1/0/1 to deny access of 802.1X users to the FTP server from 8:00 to 18:00 on weekdays.
Figure 37: Network diagram
Configuration procedure
Configure the 802.1X client. Make sure the client is able to update its IP address after the access port is assigned to the 802.1X guest VLAN or an authorization VLAN. (Details not shown.)
Configure the RADIUS servers to provide authentication, authorization, and accounting services. Add user accounts and specify the ACL (ACL 3000 in this example) for the users. (Details not shown.)
Assign an IP address to each interface, as shown in Figure 44. (Details not shown.)
Configure a RADIUS scheme:
# Create RADIUS scheme 2000 and enter RADIUS scheme view.
<Device> system-view [Device] radius scheme 2000
# Specify the server at 10.11.1.1 as the primary authentication server, and set the authentication port to 1812.
[Device-radius-2000] primary authentication 10.11.1.1 1812
# Specify the server at 10.11.1.2 as the primary accounting server, and set the accounting port to 1813.
[Device-radius-2000] primary accounting 10.11.1.2 1813
# Set the shared key to abc in plain text for secure communication between the authentication server and the device.
[Device-radius-2000] key authentication simple abc
# Set the shared key to abc in plain text for secure communication between the accounting server and the device.
[Device-radius-2000] key accounting simple abc
# Exclude the ISP domain names from the usernames sent to the RADIUS server.
[Device-radius-2000] user-name-format without-domain [Device-radius-2000] quit
Configure an ISP domain:
# Create an ISP domain named bbb and enter ISP domain view.
[Device] domain bbb
# Apply RADIUS scheme 2000 to the ISP domain for authentication, authorization, and accounting.
[Device-isp-bbb] authentication lan-access radius-scheme 2000 [Device-isp-bbb] authorization lan-access radius-scheme 2000 [Device-isp-bbb] accounting lan-access radius-scheme 2000 [Device-isp-bbb] quit
Configure a time range named ftp from 8:00 to 18:00 on weekdays.
[Device] time-range ftp 8:00 to 18:00 working-day
Configure ACL 3000 to deny packets destined for the FTP server at 10.0.0.1 during the specified time range.
[Device] acl advanced 3000 [Device-acl-ipv4-adv-3000] rule 0 deny ip destination 10.0.0.1 0 time-range ftp [Device-acl-ipv4-adv-3000] quit
Configure 802.1X:
# Enable 802.1X on GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1 [Device-GigabitEthernet1/0/1] dot1x [Device-GigabitEthernet1/0/1] quit
# Enable 802.1X globally.
[Device] dot1x
Verifying the configuration
# Use the user account to pass authentication. (Details not shown.)
# Verify that the user cannot ping the FTP server at any time from 8:00 to 18:00 on any weekday.
C:\>ping 10.0.0.1
Pinging 10.0.0.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 10.0.0.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
The output shows that ACL 3000 is active on the user, and the user cannot access the FTP server.