Basic 802.1X authentication configuration example
Network requirements
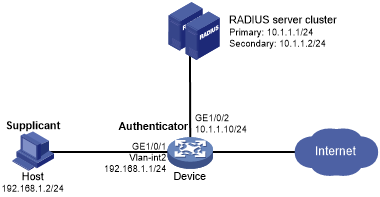
As shown in Figure 39, the access device performs 802.1X authentication for users who connect to GigabitEthernet 1/0/1. Implement MAC-based access control on the port, so the logoff of one user does not affect other online 802.1X users.
Use RADIUS servers to perform authentication, authorization, and accounting for the 802.1X users. If RADIUS authentication fails, perform local authentication on the access device.
Configure the host at 10.1.1.1/24 as the primary authentication and accounting servers, and the host at 10.1.1.2/24 as the secondary authentication and accounting servers. Assign all users to ISP domain bbb.
Set the shared key to name for packets between the access device and the authentication server. Set the shared key to money for packets between the access device and the accounting server.
Figure 35: Network diagram
Configuration procedure
Configure the 802.1X client. If HPE iNode is used, do not select the Carry version info option in the client configuration. (Details not shown.)
Configure the RADIUS servers and add user accounts for the 802.1X users. (Details not shown.)
For information about the RADIUS commands used on the access device in this example, see Security Command Reference.
Assign an IP address for each interface on the access device. (Details not shown.)
Configure user accounts for the 802.1X users on the access device:
# Add a local network access user with username localuser and password localpass in plaintext. (Make sure the username and password are the same as those configured on the RADIUS servers.)
<Device> system-view [Device] local-user localuser class network [Device-luser-network-localuser] password simple localpass
# Set the service type to lan-access.
[Device-luser-network-localuser] service-type lan-access [Device-luser-network-localuser] quit
Configure a RADIUS scheme:
# Create a RADIUS scheme named radius1 and enter RADIUS scheme view.
[Device] radius scheme radius1
# Specify the IP addresses of the primary authentication and accounting RADIUS servers.
[Device-radius-radius1] primary authentication 10.1.1.1 [Device-radius-radius1] primary accounting 10.1.1.1
# Configure the IP addresses of the secondary authentication and accounting RADIUS servers.
[Device-radius-radius1] secondary authentication 10.1.1.2 [Device-radius-radius1] secondary accounting 10.1.1.2
# Specify the shared key between the access device and the authentication server.
[Device-radius-radius1] key authentication simple name
# Specify the shared key between the access device and the accounting server.
[Device-radius-radius1] key accounting simple money
# Exclude the ISP domain names from the usernames sent to the RADIUS servers.
[Device-radius-radius1] user-name-format without-domain [Device-radius-radius1] quit
![[NOTE: ]](images/note.png)
NOTE:
The access device must use the same username format as the RADIUS server. If the RADIUS server includes the ISP domain name in the username, so must the access device.
Configure the ISP domain:
# Create an ISP domain named bbb and enter ISP domain view.
[Device] domain bbb
# Apply RADIUS scheme radius1 to the ISP domain, and specify local authentication as the secondary authentication method.
[Device-isp-bbb] authentication lan-access radius-scheme radius1 local [Device-isp-bbb] authorization lan-access radius-scheme radius1 local [Device-isp-bbb] accounting lan-access radius-scheme radius1 local [Device-isp-bbb] quit
Configure 802.1X:
# Enable 802.1X on GigabitEthernet 1/0/1.
[Device] interface gigabitethernet 1/0/1 [Device-GigabitEthernet1/0/1] dot1x
# Enable MAC-based access control on the port. By default, the port uses MAC-based access control.
[Device-GigabitEthernet1/0/1] dot1x port-method macbased
# Specify ISP domain bbb as the mandatory domain.
[Device-GigabitEthernet1/0/1] dot1x mandatory-domain bbb [Device-GigabitEthernet1/0/1] quit
# Enable 802.1X globally.
[Device] dot1x
Verifying the configuration
# Verify the 802.1X configuration on GigabitEthernet 1/0/1.
[Device] display dot1x interface gigabitethernet 1/0/1
# Display the user connection information after an 802.1X user passes authentication.
[Device] display dot1x connection