Authentication and authorization for SSH users by a RADIUS server
Network requirements
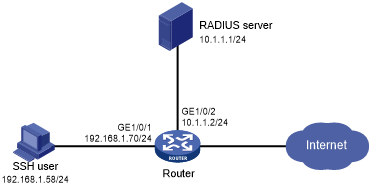
As shown in Figure 12, configure the router to meet the following requirements:
Use the RADIUS server for SSH user authentication and authorization.
Include domain names in the usernames sent to the RADIUS server.
Assign the default user role network-operator to SSH users after they pass authentication.
The RADIUS server runs on IMC. Add an account with username hello@bbb on the RADIUS server.
The RADIUS server and the router use expert as the shared key for secure RADIUS communication. The ports for authentication and accounting are 1812 and 1813, respectively.
Figure 11: Network diagram
Configuration procedure
Configure the RADIUS server on IMC 5.0:
![[NOTE: ]](images/note.png)
NOTE:
In this example, the RADIUS server runs on IMC PLAT 5.0 (E0101) and IMC UAM 5.0 (E0101).
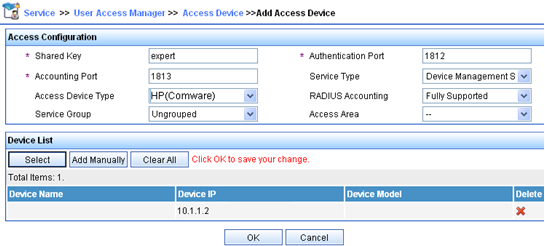
# Add the router to the IMC Platform as an access device.
Log in to IMC, click the Service tab, and select User Access Manager > Access Device Management > Access Device from the navigation tree. Then, click Add to configure an access device as follows:
Set the shared key for secure RADIUS communication to expert.
Set the ports for authentication and accounting to 1812 and 1813, respectively.
Select Device Management Service from the Service Type list.
Select HP(Comware) from the Access Device Type list.
Select the access device from the device list or manually add the access device (with IP address 10.1.1.2).
Use the default values for other parameters and click OK.
The IP address of the access device specified here must be the same as the source IP address of the RADIUS packets sent from the router. The source IP address is chosen in the following order on the router:
IP address specified by the nas-ip command.
IP address specified by the radius nas-ip command.
IP address of the outbound interface (the default).
Figure 12: Adding the router as an access device
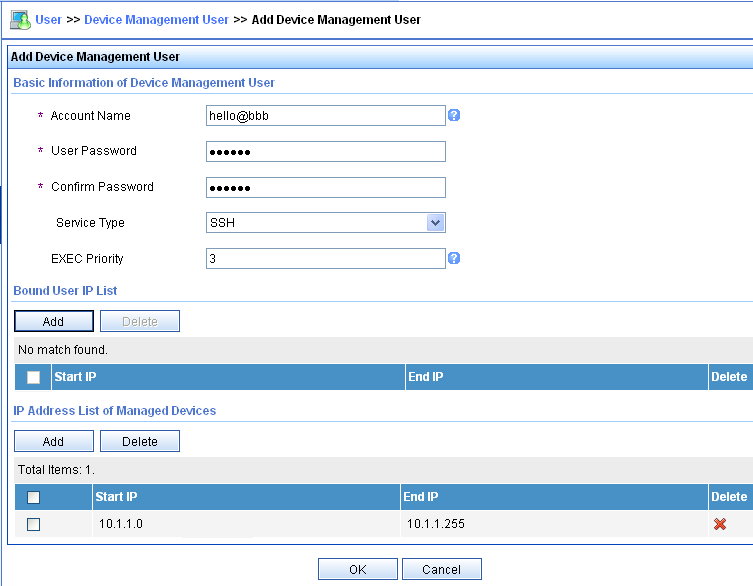
# Add an account for device management.
Click the User tab, and select Access User View > Device Mgmt User from the navigation tree. Then, click Add to configure a device management account as follows:
Enter account name hello@bbb and specify the password.
Select SSH from the Service Type list.
Specify 10.1.1.0 to 10.1.1.255 as the IP address range of hosts to be managed.
Click OK.
![[NOTE: ]](images/note.png)
NOTE:
The IP address range must contain the IP address of the router.
Figure 13: Adding an account for device management
Configure the router:
# Configure the IP address of interface GigabitEthernet 1/0/1, through which the SSH user accesses the router.
<Router> system-view [Router] interface gigabitethernet 1/0/1 [Router-GigabitEthernet1/0/1] ip address 192.168.1.70 255.255.255.0 [Router-GigabitEthernet1/0/1] quit
# Configure the IP address of interface GigabitEthernet 1/0/2, through which the router communicates with the server.
[Router] interface gigabitethernet 1/0/2 [Router-GigabitEthernet1/0/2] ip address 10.1.1.2 255.255.255.0 [Router-GigabitEthernet1/0/2] quit
# Create local RSA and DSA key pairs.
[Router] public-key local create rsa [Router] public-key local create dsa
# Enable the SSH service.
[Router] ssh server enable
# Enable scheme authentication for user lines VTY 0 through VTY 63.
[Router] line vty 0 63 [Router-line-vty0-63] authentication-mode scheme [Router-line-vty0-63] quit
# Enable the default user role feature to assign authenticated SSH users the default user role network-operator.
[Router] role default-role enable
# Create a RADIUS scheme.
[Router] radius scheme rad
# Specify the primary authentication server.
[Router-radius-rad] primary authentication 10.1.1.1 1812
# Set the shared key to expert in plaintext form for secure communication with the server.
[Router-radius-rad] key authentication simple expert
# Include domain names in the usernames sent to the RADIUS server.
[Router-radius-rad] user-name-format with-domain [Router-radius-rad] quit
# Create an ISP domain named bbb and configure authentication, authorization, and accounting methods for login users. Because RADIUS user authorization information is piggybacked in authentication responses, the authentication and authorization methods must use the same RADIUS scheme.
[Router] domain bbb [Router-isp-bbb] authentication login radius-scheme rad [Router-isp-bbb] authorization login radius-scheme rad [Router-isp-bbb] accounting login none [Router-isp-bbb] quit
Verifying the configuration
# Initiate an SSH connection to the router, and enter username hello@bbb and the correct password. The user logs in to the router. (Details not shown.)
# Verify that the user can use the commands permitted by the network-operator user role. (Details not shown.)