Security zone configuration example
Network requirements
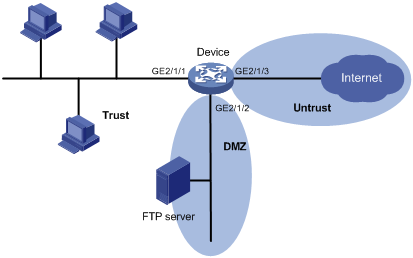
As shown in Figure 39, a firewall (Device) connects the corporate network to the Internet. The corporate network needs to provide FTP services for external users.
To ensure corporate network security, configure the firewall as follows:
Assign the interfaces used to connect the internal network, the servers, and the Internet to security zones Trust, DMZ, and Untrust, respectively.
Configure zone pairs and apply object policies to control access as follows:
Allow internal users to access the FTP server and the Internet.
Allow external users to access the FTP server.
Allow the FTP server to access the Internet.
Deny external users and the FTP server access to the internal network.
Figure 39: Network diagram
Configuration procedure
# Add interface GigabitEthernet 2/1/1 to security zone Trust.
<Device> system-view [Device] security-zone name trust [Device-security-zone-Trust] import interface gigabitethernet 2/1/1 [Device-security-zone-Trust] quit
# Add interface GigabitEthernet 2/1/2 to security zone DMZ.
[Device] security-zone name dmz [Device-security-zone-DMZ] import interface gigabitethernet 2/1/2 [Device-security-zone-DMZ] quit
# Add interface GigabitEthernet 2/1/3 to security zone Untrust.
[Device] security-zone name untrust [Device-security-zone-Untrust] import interface gigabitethernet 2/1/3 [Device-security-zone-Untrust] quit
# Configure ACL 3500 to permit IP traffic.
[Device] acl advanced 3500 [Device-acl-ipv4-3500] rule permit ip [Device-acl-ipv4-3500] quit
# Configure ASPF policy 1 to detect FTP traffic. To detect other types of traffic, use the detect command to add the protocols.
[Device] aspf policy 1 [Device-aspf-policy-1] detect ftp [Device-aspf-policy-1] quit
# Create a zone pair with the source security zone Trust and destination security zone Untrust.
[Device] zone-pair security source trust destination untrust
# Apply ASPF policy 1 and ACL 3500 to the zone pair.
[Device-zone-pair-security-Trust-Untrust] aspf apply policy 1 [Device-zone-pair-security-Trust-Untrust] packet-filter 3500 [Device-zone-pair-security-Trust-Untrust] quit
# Create a zone pair with the source security zone Trust and destination security zone DMZ.
[Device] zone-pair security source trust destination dmz
# Apply ASPF policy 1 and ACL 3500 to the zone pair.
[Device-zone-pair-security-Trust-DMZ] aspf apply policy 1 [Device-zone-pair-security-Trust-DMZ] packet-filter 3500 [Device-zone-pair-security-Trust-DMZ] quit
Verifying the configuration
# Verify that internal hosts can access resources on the Internet and the FTP resources in the DMZ zone. (Details not shown.)
# Verify that access requests initiated from the Internet or the DMZ zone are denied. (Details not shown.)