Loop protection
In cases where spanning tree protocols cannot be used to prevent loops at the edge of the network, loop protection may provide a suitable alternative. Loop protection can find loops in untagged layer 2 links, as well as on tagged VLANs.
The cases where loop protection might be chosen ahead of spanning tree to detect and prevent loops are:
- On ports with client authentication: When spanning tree is enabled on a switch that uses 802.1X, web authentication, or MAC authentication, loops may go undetected. For example, spanning tree packets that are looped back to an edge port will not be processed because they have a different broadcast/multicast MAC address from the client-authenticated MAC address. To ensure that client-authenticated edge ports get blocked when loops occur, you should enable loop protection on those ports.
- On ports connected to unmanaged devices: Spanning tree cannot detect the formation of loops where there is an unmanaged device on the network that does not process spanning tree packets and simply drops them. Loop protection has no such limitation, and can be used to prevent loops on unmanaged switches.
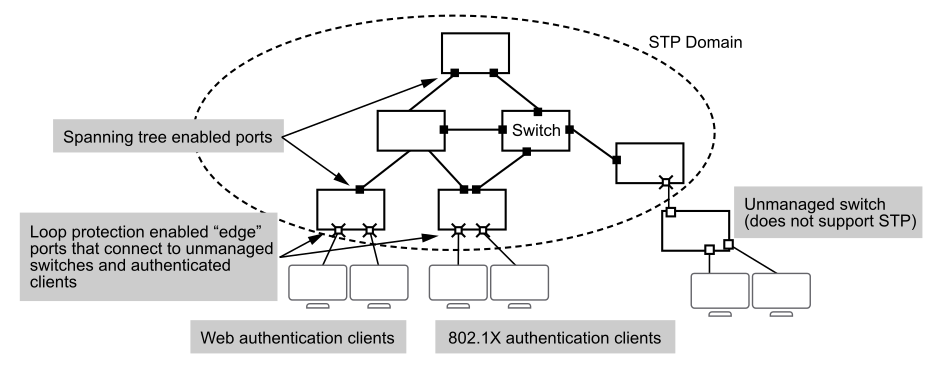
Loop protection finds loops by sending loop protection packets on each port, LAG, or VLAN on which loop protection is enabled. If a loop protection packet is received by the same switch that sent it, it indicates a loop exists and one of the following actions is taken:
- Discovery of the loop is logged but port states are not changed.
- The sending port is disabled.
- The sending and receiving ports are both disabled.