Scenario 1
This example illustrates how an 8325 switch can be connected to a VMware NSX.
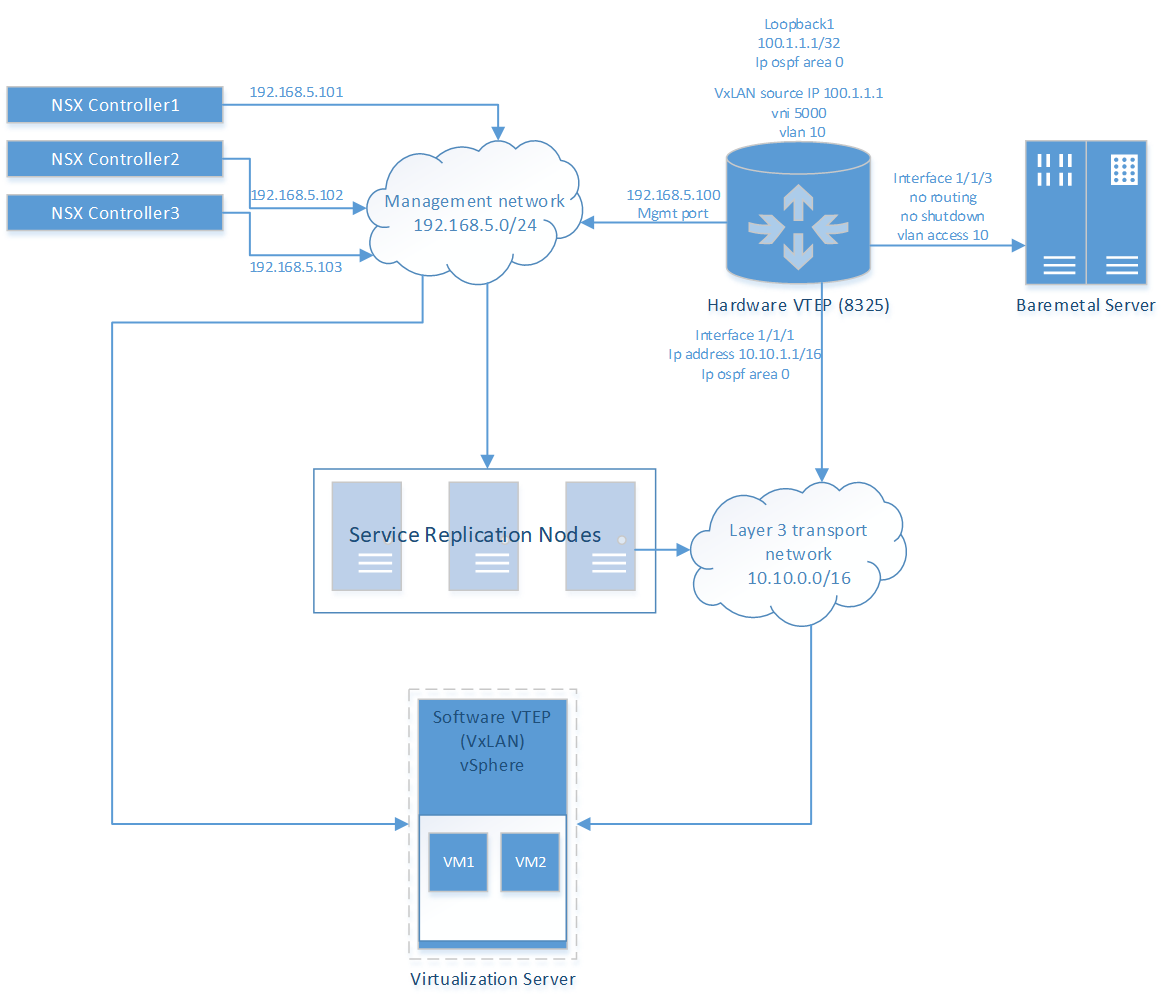
Key components
NSX controllers: Central control point for all logical switches in the network.
Management network: Network on which the 8325 switch communicates with the NSX controllers.
Hardware VTEP (8325 switch): Communication with the NSX controller occurs via the switch management port (which operates as a DHCP client by default). Interface 1/1/1 links the switch to the layer 3 network. Interface 1/1/3 extends the layer 2 domain over a VXLAN and links the switch to the bare metal server. OSPF is used to enable the routed layer 3 underlay network.
Bare metal server: Physical server providing network services.
Layer 3 transport network: The underlay network which provides routing functionality.
Virtualization server: The virtualization server is managed by VMWare VSphere. It hosts software VTEPs which perform VXLAN encapsulation for VMs deployed in virtual servers (such as an ESXi server).