Permitting traffic filtered through multiple ACLs
On a given interface where multiple ACLs apply to the same traffic, a packet having a match with a
deny ACE in any applicable ACL on the interface (including an implicit
deny any any) is dropped.
Ports 10 and 12 belong to VLAN 100.
A static port ACL filtering inbound IPv6 traffic is configured on port 10.
A VACL (with a different set of ACEs) is configured on VLAN 100.
An RACL is also configured for inbound, routed traffic on VLAN 100.
An inbound switched packet entering on port 10, with a destination on port 12, will be screened first by the VACL and then by the static port ACL and the RACL. A match with a
deny action (including an implicit deny) in any of the applicable ACLs causes the switch to drop the packet. If the packet has a match with explicit
deny ACEs in multiple ACLs and the log option is included in these ACEs, a log event for that denied packet occurs in each ACL where there is an applicable "deny" ACE. Logging can also be enabled for matches with "permit" ACEs.
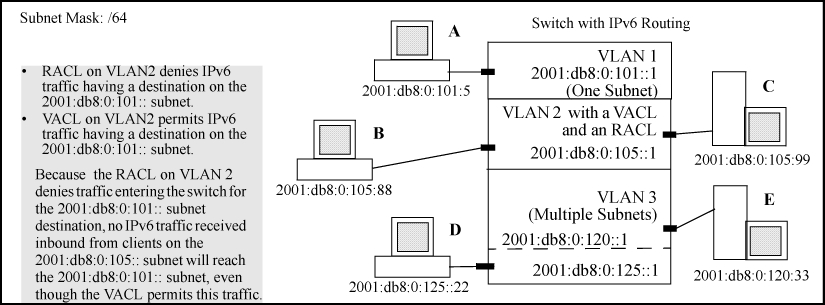
A VACL permitting IPv6 traffic having a destination on the 2001:db8:0:101:: subnet
An RACL that denies inbound IPv6 traffic having a destination on the 2001:db8:0:101:: subnet
In this case, no routed IPv6 traffic received on the switch from clients on the 2001:db8:0:105:: subnet will reach the 2001:db8:0:101:: subnet, even though the VACL allows such traffic. This is because the RACL is configured with a
deny ACE that causes the switch to drop the traffic regardless of whether the VACL permits the traffic.
Software release K.15.01 supports connection-rate ACLs for inbound IPv4 traffic, but not for IPv6 traffic.
In cases where an RACL and any type of port or VLAN ACL are filtering traffic entering the switch, the switched traffic explicitly permitted by the port or VLAN ACL is not filtered by the RACL (except when the traffic has a destination on the switch itself). However, routed traffic explicitly permitted by the port or VLAN ACL (and switched traffic having a destination on the switch itself) must also be explicitly permitted by the RACL, or it will be dropped.
A switched packet is not affected by an outbound RACL assigned to the VLAN on which the packet exits the switch.
Beginning with software release K.14.01, static ACL mirroring and static ACL rate-limiting are deprecated in favor of classifier-based mirroring and rate-limiting features that do not use ACLs. If ACL mirroring or ACL rate-limiting is already configured in a switch running software version K.13.xx, downloading and booting from release K.14.01 or greater automatically modifies the deprecated configuration to conform to the classifier-based mirroring and rate-limiting supported in release K.14.01 or greater. For more information on this topic, see the latest Aruba-OS Switch Advanced Traffic Management Guide for your switch.