Permitting traffic filtered through multiple ACLs (example)
On a given interface where multiple ACLs apply to the same traffic, a packet having a match with a
deny ACE in any applicable ACL on the interface (including an implicit
deny any any) is dropped.
Ports 10 and 12 belong to VLAN 100.
A static port ACL filtering inbound or outbound IPv6 traffic is configured on port 10.
A VACL (with a different set of ACEs) is configured on VLAN 100.
An inbound packet entering on port 10, with a destination on port 12, will be screened by the static port ACL and the VACL, regardless of a match with any
permit or
deny action. A match with a
deny action (including an implicit deny) in either ACL will cause the switch to drop the packet. (If the packet has a match with explicit
deny ACEs in multiple ACLs and the log option is included in these ACEs, then a separate log event will occur for each match.)
An inbound, switched packet entering on port 10, with a destination on port 12, will be screened first by the VACL and then by the static port ACL. A match with a
deny action (including an implicit deny) in any of the applicable ACLs causes the switch to drop the packet. If the packet has a match with explicit
deny ACEs in multiple ACLs and the log option is included in these ACEs, then a log event for that denied packet will occur in each ACL where there is an applicable “deny” ACE.
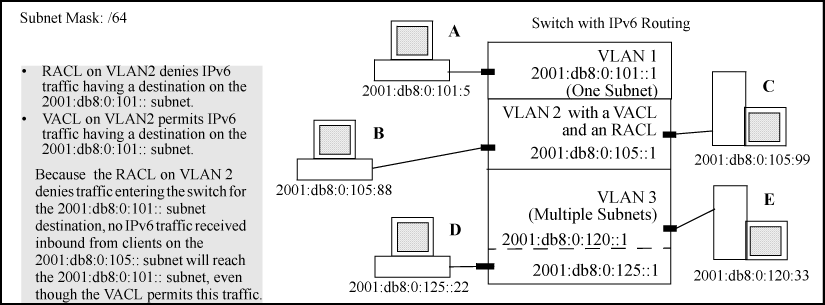
However, in this case, suppose that VLAN 2 in the following figure is configured with a VACL permitting IPv6 traffic having a destination on the 2001:db8:0:101:: subnet.
In this case, no routed IPv6 traffic received on the switch from clients on the 2001:db8:0:105:: subnet will reach the 2001:db8:0:101:: subnet, even though the VACL allows such traffic.
This software supports connection-rate ACLs for inbound IPv4 traffic, but not for IPv6 traffic.