Remote gateway case
Configuring ACL "101" (example below) and applying it outbound on VLAN 1 in the figure below includes the router gateway (10.0.8.1) needed by devices on other networks. This can prevent the switch from sending ARP and other messages to the gateway router to support traffic from authorized remote networks.
In Figure 45: Inadvertently blocking a gateway, this ACE (see data in bold below) denies access to the 10 Net's 10.0.8.1 router gateway needed by the 20 Net (Subnet mask is 255.255.255.0).See: example
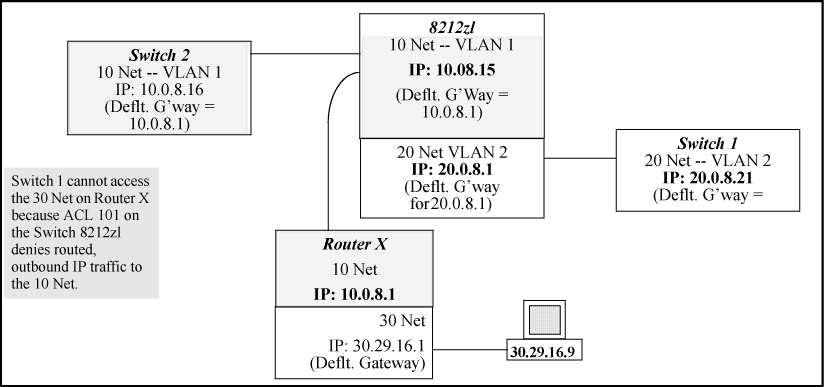
To avoid inadvertently blocking the remote gateway for authorized traffic from another network (such as the 20 Net in this Example:):
Procedure
- Configure an ACE that specifically permits authorized traffic from the remote network.
- Configure narrowly defined ACEs to block unwanted IP traffic that would otherwise use the gateway; such ACEs might deny traffic for a particular application, particular hosts, or an entire subnet.
- Configure a "permit any" ACE to specifically allow any IP traffic to move through the gateway.
ACE blocking an entire subnet
switch(config)# access-list config ip access-list extended "101" deny ip 0.0.0.0 255.255.255.255 10.0.8.30 0.0.0.255 permit ip 0.0.0.0 255.255.255.255 0.0.0.00 255.255.255.255 exit