Option B: Configuring the switch for client Public-Key SSH authentication
Using this option results in the switch also authenticating the client's public key.
If configured with this option, the switch uses its public key to authenticate itself to a client, but the client must also provide a client public key for the switch to authenticate. This option requires the additional step of copying a client public-key file from a TFTP or SFTP server into the switch.
With the prerequisite steps complete and SSH properly configured on the switch, if an SSH client contacts the switch, login authentication automatically occurs first, using the switch and client public keys. After the client gains login access, the switch controls client access to the manager level by requiring the passwords configured earlier by the
aaa authentication ssh enable command.
Hewlett Packard Enterprise recommends that you always assign a manager-level (enable) password to the switch. Without this level of protection, any user with Telnet, web, or serial port access to the switch can change the switch configuration. If you configure only an operator password, entering the operator password through telnet, web, ssh or serial port access enables full manager privileges. See 1.
Before you can use this option, you must do the following:
Create a key pair on an SSH client.
Copy the client's public key into a public-key file (which can contain up to 10 client public keys.)
Copy the public-key file into a TFTP or SFTP server accessible to the switch and download the file to the switch.
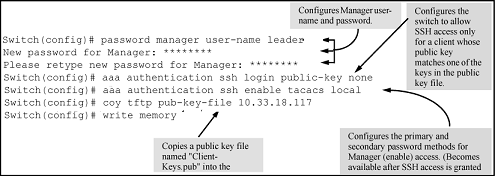
Configuring for SSH access requiring a client public-key match and manager passwords
Assume you have a client public-key file named Client-Keys.pub (on a TFTP server at 10.33.18.117) ready for downloading to the switch:
For SSH access to the switch allow only clients having a private key that matches a public key found in Client-Keys.pub.
For manager-level (enable) access for successful SSH clients, use TACACS+ for primary password authentication and
localfor secondary password authentication, with a manager username of "leader" and a password of "m0ns00n".
To set up this operation, configure the switch in a manner similar to the following illustration:
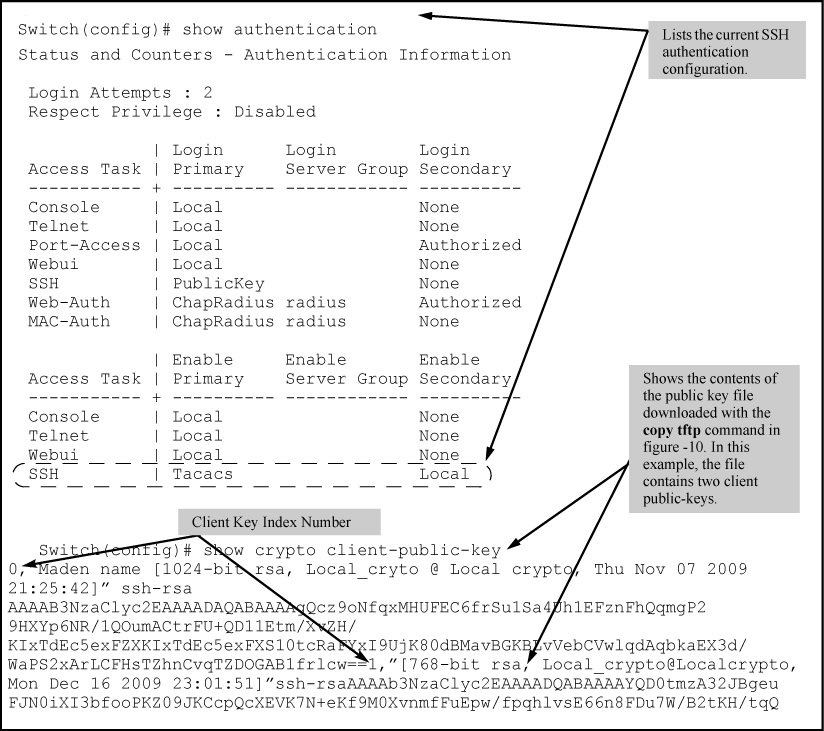
The following illustration shows how to check the results of the above commands.