Registering HTTP redirect
Procedure
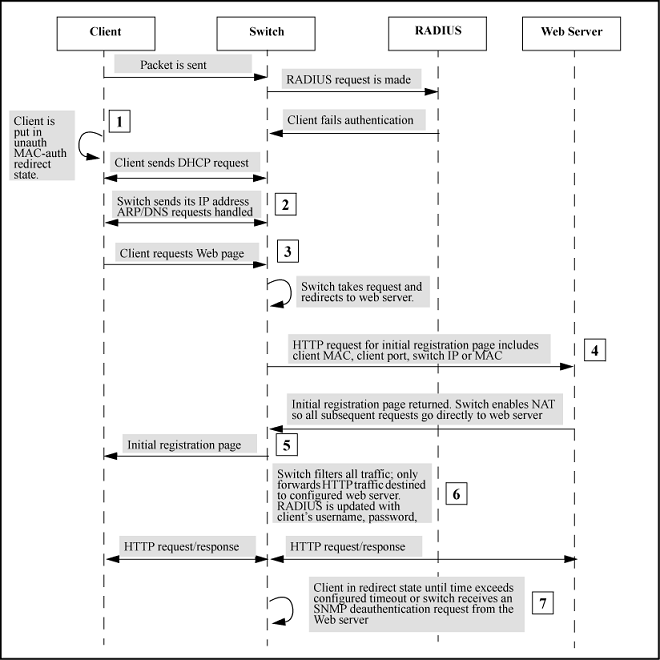
- When the redirect feature is enabled, a client that fails MAC authentication is moved into the unauthorized MAC authentication redirection state.
- A client in the redirect state (having failed MAC authentication) with a web browser open sends a DHCP request. The switch responds with a DHCP lease for an address in the switch configurable DHCP address range. Additionally, the switch IP address becomes the client’s default gateway. All ARP/DNS requests are handled by the switch and all requests are directed to the switch. The switch replies to these requests with its own address.
- The client requests a web page. The switch takes this request and responds to the client browser with an HTTP redirect to the configured URL. The client MAC address and interface port are appended as HTTP parameters.
- Before returning the initial registration page to the client, the switch enables NAT so that all subsequent requests go to the web server directly. The initial HTML page is returned to the switch and then by proxy to the client.
- After the registration process completes, the registration server updates the RADIUS server with the client’s user name, password, and profile.
- The client remains in the redirect state until the client’s time exceeds the configured timeout or the switch receives an SNMP deauthentication request from the registration server.
- The registration server sends an SNMP request to the switch with the MAC identification and interface port to reauthenticate or deauthenticate the client.
- The switch moves the client out of the special web-based/MAC authentication redirect state and the client becomes unknown to the switch again. This sets the stage for a new MAC authentication cycle.