RACL applications
RACLs filter routed IPv4 traffic entering or leaving the switch on VLANs configured with the "in" and "out" ACL option
Syntax
vlan vid ip access-group identifier {<in | out>}
Assign either an inbound ACL on VLAN 1 or an outbound ACL on VLAN 2 to filter a packet routed between subnets on different VLANs; that is, from the workstation 10.28.10.5 on VLAN 1 to the server at 10.28.20.99 on VLAN 2. An outbound ACL on VLAN 1 or an inbound ACL on VLAN 2 would not filter the packet.
Where multiple subnets are configured on the same VLAN, use either inbound or outbound ACLs to filter routed IPv4 traffic between the subnets on the VLAN. Traffic source and destination IP addresses must be on devices external to the switch.
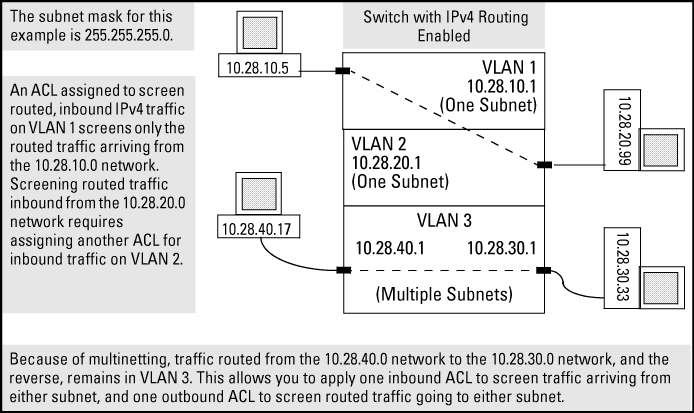
The switch allows one inbound RACL assignment and one outbound RACL assignment configured per VLAN. This is in addition to any other ACL assigned to the VLAN or to any ports on the VLAN. You can use the same RACL or different RACLs to filter inbound and outbound routed traffic on a VLAN.
RACLs do not filter IPv4 traffic that remains in the same subnet from source to destination (switched traffic) unless the destination address (DA) or source address (SA) is on the switch itself.