Commands for applying an ACL with logging
Switch(config)# ipv6 access-list NO-TELNET
Switch(config-ipv6-acl)# remark "deny fe80::10:3 Telnet traffic."
Switch(config-ipv6-acl)# deny tcp host fe80::10:3 any eq telnet log
Switch(config-ipv6-acl)# permit ipv6 any any
Switch(config-ipv6-acl)# exit
Switch(config)# vlan 10 ipv6 access-group NO-TELNET vlan 1
Switch(config)# logging 10.10.50.173
Switch(config)# logging facility syslog
Switch(config)# debug destination logging
Switch(config)# debug destination session
Switch(config)# debug acl
Switch(config)# write mem
Switch(config)# show debug
Debug Logging
Destination:
Logging --
10.10.50.173
Facility = syslog
Severity = debug
System Module = all-pass
Priority Desc =
Session
Enabled debug types:
event
acl log
Switch(config)# show access-list NO-TELNET config
ipv6 access-list "NO-TELNET"
10 remark "deny fe80::10:3 TELNET TRAFFIC"
10 deny tcp fe80::10:3/128 ::/0 eq 23 log
20 permit ipv6 ::/0 ::/0
exit1 Assigns the ACL named "NOTELNET" as a VACL to filter Telnet traffic from FE80::10:3 entering the switch on VLAN 10
ACL log application
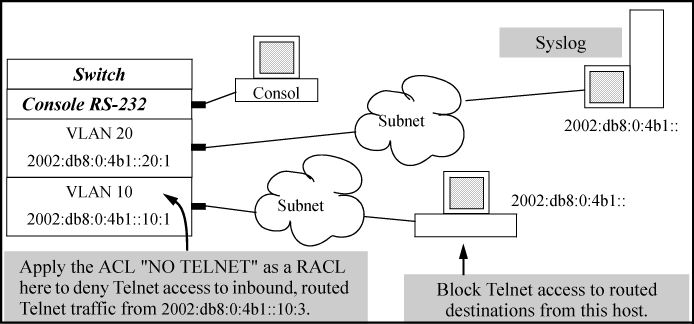
For VLAN 10, configure an ACL with an ACL-ID of "NO-TELNET" and use the RACL
inoption to deny Telnet traffic entering the switch from IP address 2001:db8:0:4b1::10:3 to any routed destination. (This assignment will not filter Telnet traffic from 2001:db8:0:4b1::10:3 to destinations on VLAN 10 itself.)Configure the switch to send an ACL log message to the current console session and to a syslog server at 2001:db8:0:4b1::20:3 on VLAN 20 if the switch detects a packet match denying a Telnet attempt from 2001:db8:0:4b1::10:3.
(This example assumes that IPv6 routing is already configured on the switch.)