Example of how the mask bit settings define a match
Assume an ACE where the second octet of the mask for an SA is 7 (the rightmost three bits are "on", or "1") and the second octet of the corresponding SA in the ACE is 31 (the rightmost five bits). In this case, a match occurs when the second octet of the SA in a packet being filtered has a value in the range of 24 to 31.
Location of octet |
Bit position in the octet |
|||||||
|---|---|---|---|---|---|---|---|---|
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
|
SA in ACE |
0 |
0 |
0 |
1 |
1 |
1 |
1 |
1 |
Mask for SA |
0 |
0 |
0 |
0 |
0 |
1 |
1 |
1 |
Corresponding Octet of a Packet's SA |
0 |
0 |
0 |
1 |
1 |
0/1 |
0/1 |
0/1 |
The shaded area indicates bits in the packet that must exactly match the bits in the source address in the ACE. Wherever the mask bits are ones (wildcards), the corresponding address bits in the packet can be any value, and where the mask bits are zeros, the corresponding address bits in the packet must be the same as those in the ACE. Note: This example covers only one octet of an IPv4 address. An actual ACE applies this method to all four octets of the address. |
||||||||
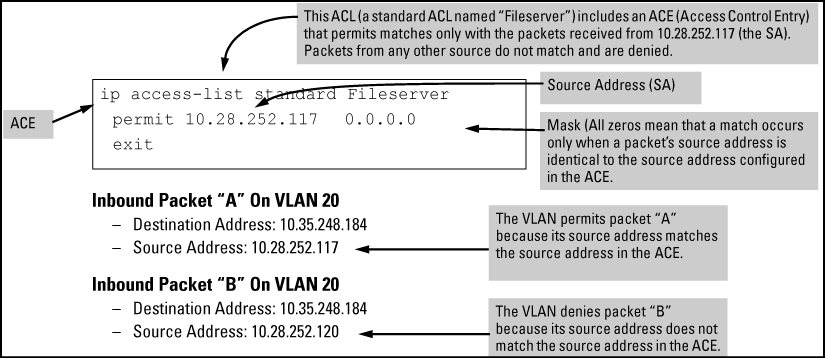
Example of allowing only one IPv4 address ("host" option)
Suppose, for example, that you have configured an ACL to filter inbound packets on VLAN 20. Because the mask is all zeros, the ACE policy dictates that a match occurs only when the source address on such packets is identical to the address configured in the ACE.
Examples allowing multiple IPv4 addresses
The following table provides examples of how to apply masks to meet various filtering requirements.
Address in the ACE |
Mask |
Policy for a match between a packet and the ACE |
Allowed addresses |
|---|---|---|---|
A: 10.38.252.195 |
0.0.0.255 |
Exact match in first three octets only. |
10.38.252.<0-255> |
B: 10.38.252.195 |
0.0.7.255 |
Exact match in the first two octets and the leftmost five bits (248) of the third octet. |
10.38.<248-255> .<0-255>(In the third octet, only the rightmost three bits are wildcard bits. The leftmost five bits must be a match, and in the ACE, these bits are all set to 1.) |
C: 10.38.252.195 |
0.0.0.0 |
Exact match in all octets. |
10.38.252.195(There are no wildcard bits in any of the octets. |
D: 10.38.252.195 |
0.15.255.255 |
Exact match in the first octet and the leftmost four bits of the second octet. |
10.<32-47> .<0-255> .<0-255>(In the second octet, the rightmost four bits are wildcard bits.) |
Addr |
Octet |
Mask |
Octet range |
128 |
64 |
32 |
16 |
8 |
4 |
2 |
1 |
|---|---|---|---|---|---|---|---|---|---|---|---|
A |
3 |
0 all bits |
252 |
1 |
1 |
1 |
1 |
1 |
1 |
0 |
0 |
B |
3 |
7 last 3 bits |
248-255 |
1 |
1 |
1 |
1 |
1 |
0 or 1 |
0 or 1 |
0 or 1 |
C |
4 |
0 all bits |
195 |
1 |
1 |
0 |
0 |
0 |
0 |
1 |
1 |
D |
2 |
15 last 4 bits |
32-47 |
0 |
0 |
1 |
0 |
0 or 1 |
0 or 1 |
0 or 1 |
0 or 1 |
Shaded areas indicate bit settings that must be an exact match. |
|||||||||||
If there is a match between the policy in the ACE and the IPv4 address in a packet, the packet is either permitted or denied according to how the ACE is configured. If there is no match, the next ACE in the ACL is applied to the packet. The same operation applies to a destination IPv4 address used in an extended ACE.
Where an ACE includes both source and destination addresses, there is one address/ACL-mask pair for the source address, and another address/ACL-mask pair for the destination address. See Configuring named, standard ACLs.