Example
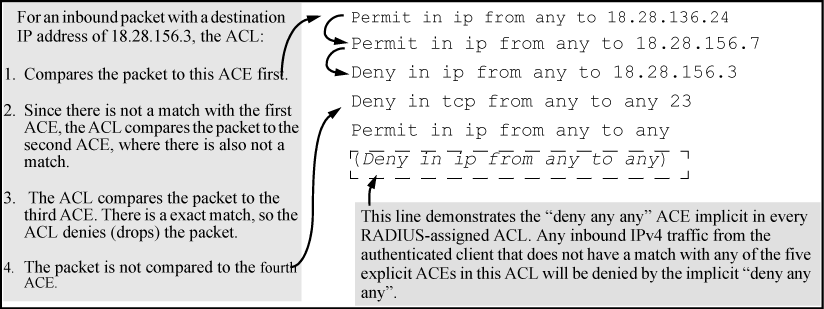
As shown above, the ACL tries to apply the first ACE in the list. If there is no match it tries the second ACE, and so on. When a match is found, the ACL invokes the configured action for that entry (permit or drop the packet) and no further comparisons of the packet are made with the remaining ACEs in the list.
This means that when an ACE whose criteria matches a packet is found, the action configured for that ACE is invoked, and any remaining ACEs in the ACL are ignored. Because of this sequential processing, successfully implementing an ACL depends in part on configuring ACEs in the correct order for the overall policy you want the ACL to enforce.
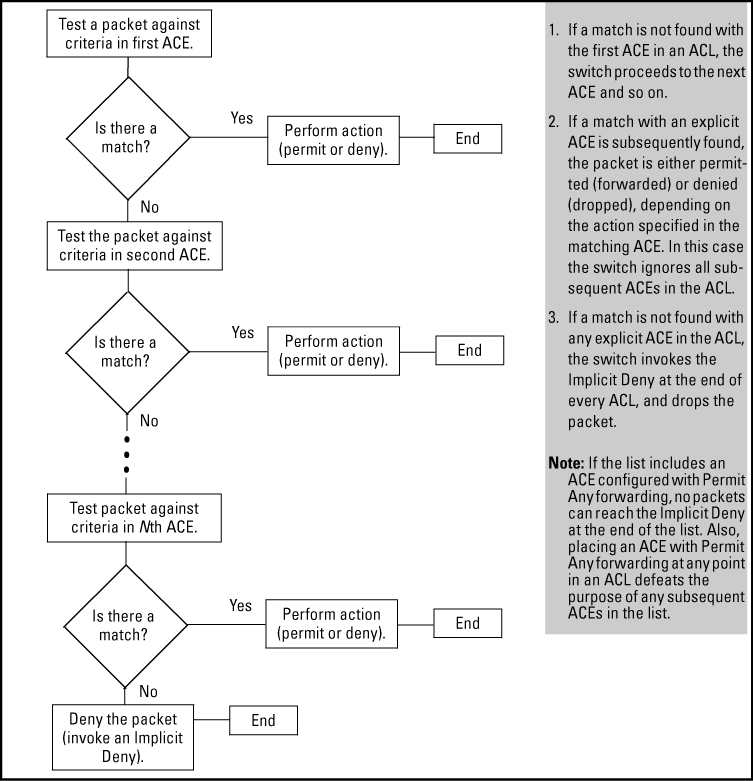
The order in which an ACE occurs in an ACL is significant.
For example, if an ACL contains six ACEs, but the first ACE allows Permit Any forwarding, then the ACL permits all IPv4 traffic, and the remaining
ACEs in the list do not apply, even if they specify criteria that would make a match with any of the traffic permitted by the first ACE.
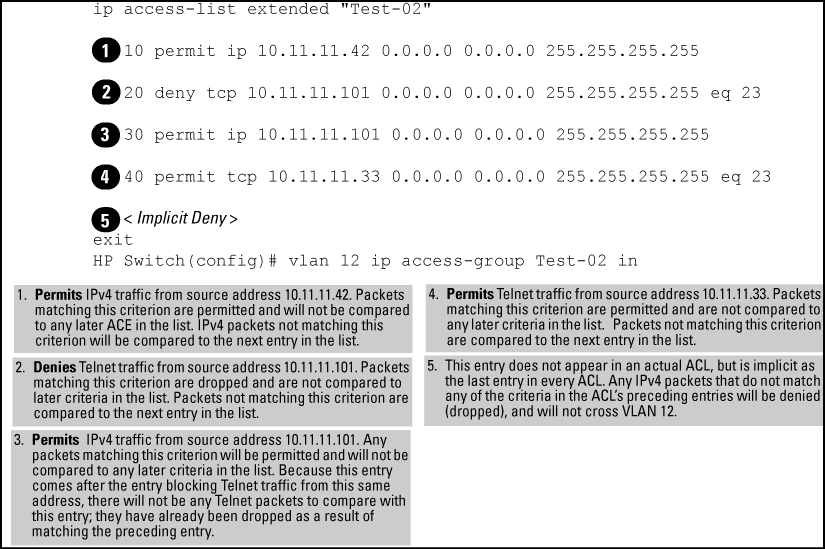
For example, suppose you want to configure an ACL on the switch (with an ID of "Test-02") to invoke these policies for routed traffic entering the switch on VLAN 12:
- Permit inbound IPv4 traffic from IP address 10.11.11.42.
- Deny only the inbound Telnet traffic from address 10.11.11.101.
- Permit only inbound Telnet traffic from IP address 10.11.11.33.
- Deny all other inbound IPv4 traffic.
The following ACL model , when assigned to inbound filtering on an interface, supports the above case:
It is important to remember that all IPv4 ACLs
configurable on the switch include an implicit deny
ip any. That is, IPv4 packets that the ACL does not explicitly permit
or deny is implicitly denied, and therefore dropped
instead of forwarded on the interface. If you want topreempt the implicit deny so that IPv4 packets not explicitly
denied by other ACEs in the ACL are permitted, insert an explicit
"permit any" as the last ACE in the ACL. Doing so permits
any packet not explicitly denied by earlier entries.
This solution does not apply in the preceding example, where the intention is for the switch to forward only explicitly permitted IPv4 packets routed on VLAN 12.