Viewing specific ACL configuration details
This command displays a specific IPv6 or IPv4 ACL configured in the running config file in an easy-to-read tabular format.
This information also appears in the
show running display. If you execute
write memory after configuring an ACL, it also appears in the
show config display.
Syntax:
show access-list <identifier> [config]
Displays detailed information on the content of a specific ACL configured in the running-config file.
For example, suppose you configured the following two ACLs in the switch:
Identifier |
Type |
Desired action |
|---|---|---|
Accounting |
IPv6 |
|
List-120 |
IPv4 Extended |
|
The following
show access-list <identifier> command shows a specific IPv6 ACL:
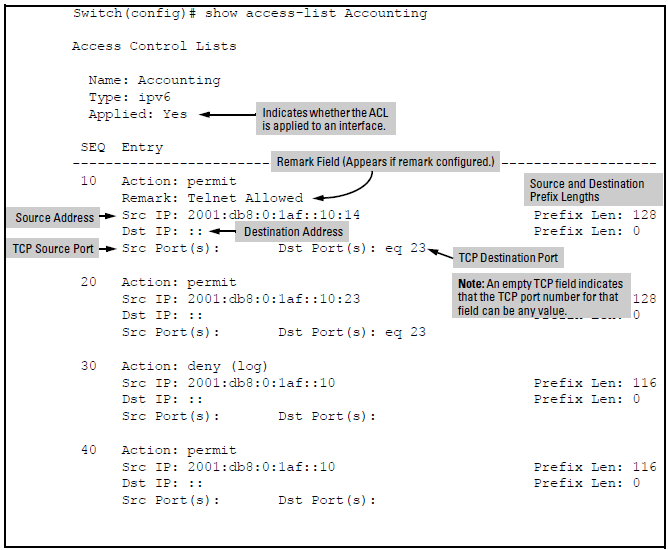
The following
show access-list <identifier> command shows a specific IPv4 ACL:
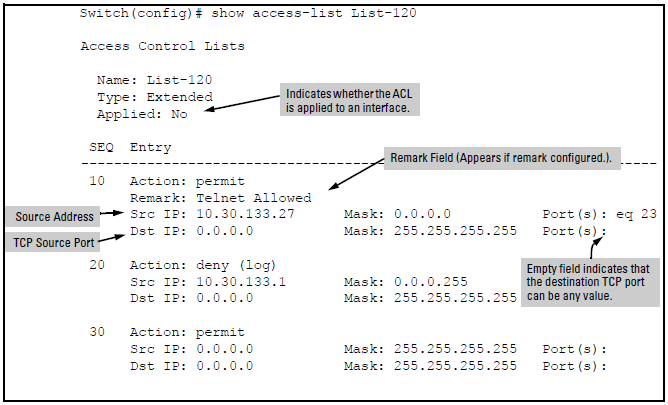
The
show access-list <identifier> config
command shows the same ACL data as
show access-list <identifier
but in the format used by the
show <run|config> commands to list the switch configuration. For example:
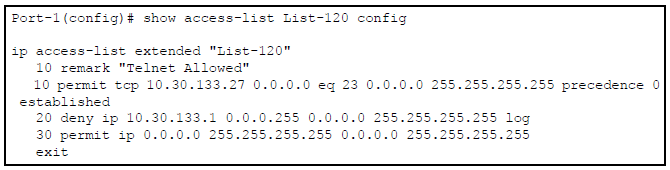
Field |
Description |
|---|---|
Name |
The ACL identifier. Can be a number from 1 to 199, or a name. |
Type |
Standard or Extended. The former uses only source IPv4 addressing. The latter uses both source and destination IPv4 addressing and also allows TCP or UDP port specifiers. |
Applied |
"Yes" means the ACL has been applied to a port or VLAN interface. "No" means the ACL exists in the switch configuration, but has not been applied to any interface, and is therefore not in use. |
SEQ |
The sequential number of the Access Control Entry (ACE) in the specified ACL. |
Entry |
Lists the content of the ACEs in the selected ACL. |
Action |
Permit (forward) or deny (drop) a packet when it is compared to the criteria in the applicable ACE and found to match. Includes the optional log option, if used, in deny actions. |
Remark |
Displays any optional remark text configured for the selected ACE. |
IP |
Used for Standard ACLs: The source IPv4 address to which the configured mask is applied to determine whether there is a match with a packet. |
Src IP |
Used for Extended ACLs: Same as above. |
Dst IP |
Used for Extended ACLs: The source and destination IPv4 addresses to which the corresponding configured masks are applied to determine whether there is a match with a packet. |
Mask |
The mask configured in an ACE and applied to the corresponding IPv4 address in the ACE to determine whether a packet matches the filtering criteria. |
Proto |
Used only in extended ACLs to specify the packet protocol type to filter. Must be either IPv4, TCP, or UDP. For TCP protocol selections, includes the
|
Port(s) |
Used only in extended ACLs to show any TCP or UDP operator and port number(s) included in the ACE. |
TOS |
Used only in extended ACLs to indicate Type-of-Service setting, if any. |
Precedence |
Used only in extended ACLs to indicate the IP precedence setting, if any. |