Overview
TACACS AAA systems are used as a single point of management to configuring and store user accounts. They are often coupled with directories and management repositories, simplifying the set up maintenance of the end-user accounts.
In the authorization function of the AAA system, network devices with Authentication Services can provide fine-grained control over user capabilities for the duration of the user’s session, for example setting access control or session duration. Enforcement of restrictions to a user account can limit available commands and levels of access.
TACACS+ authentication enables you to use a central server to allow or deny access to switches and other TACACS-aware devices in your network. This allows use of a central database to create multiple unique username/password sets with associated privilege levels, for use by individuals accessing the switch from either its console port (local access) or Telnet (remote access).
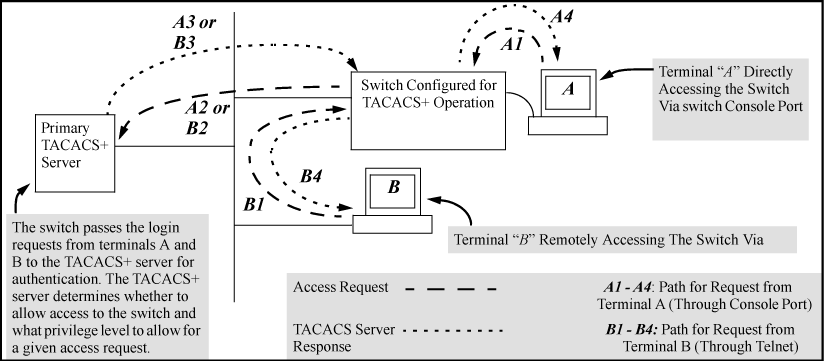
TACACS+ in the switches covered in this guide manages authentication of logon attempts through either the Console port or Telnet. TACACS+ uses an authentication hierarchy consisting of (1) remote passwords assigned in a TACACS+ server and (2) local passwords configured on the switch. That is, with TACACS+ configured, the switch first tries to contact a designated TACACS+ server for authentication services. If the switch fails to connect to any TACACS+ server, it defaults to its own locally assigned passwords for authentication control (if configured to do so). For both Console and Telnet access you can configure a login (read-only) and an enable (read/write) privilege level access.
TACACS+ does not affect WebAgent access. See Controlling WebAgent access when using TACACS+ authentication